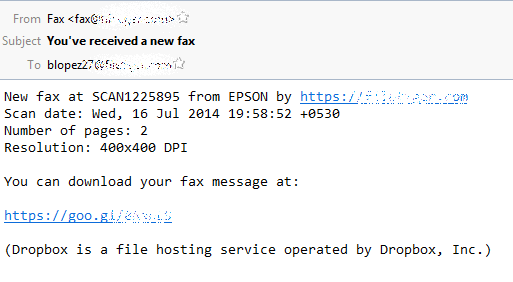
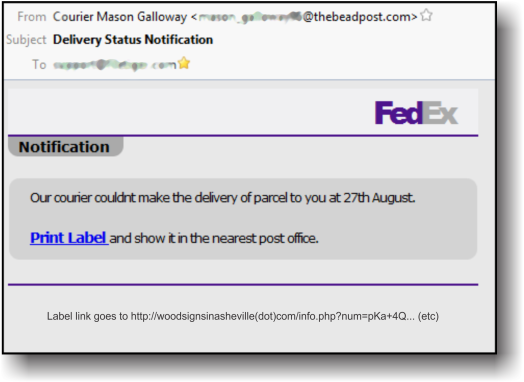
From the SPAM pile this morning…
Dear Friend,
It is with trust and sincerity that I approach you for assistance to transfer some funds into your bank account. Please do accept my apology if my mail infringes on your personal ethics. My name is Augustine Dinga, A Private Lawyer based here in Johannesburg South Africa. Honestly it will be my humble pleasure if we can work together.
I would like you to act as the next of kin to my deceased client, a citizen of your country that has the same last name with you who made a deposit of $23.5 million only with a Bank here in Johannesburg few years back. He died in a plane crash with his immediate family in a plane crash without any registered next of kin and as such the funds now have an open beneficiary mandate with a Bank, This means that any person from your country can act as the next of kin of the deceased person for claiming the inheritance funds without any risk involved.
Moreso, I have received official letter from the bank suggesting a likely proceeding for confiscation of the Fund in line with existing laws by the bank in which my client deposited the sum of $23.5 Million Dollars . According to the Government Law as provided in section 129 sub 63(N), South African Banking Edit of 1961 at the expiration of 11 years the fund will revert to the ownership of the South African Government, if nobody applies to claim the fund.
My proposition to you is to present you to the bank as the Next of kin and beneficiary of my deceased client so that the bank will pay this $23.5 million to you so that we can share the amount on a mutually agreed percentage of 60% for me 40% for you.
All legal documents to back up your claim as the deceased Next of Kin will be provided by me. All I require is your honest cooperation to enable us see this transaction through. I guarantee you that this will be executed under a legitimate arrangement that will protect you from any breach of the law.
If you are interested in this transactions, Please do let me know immediately so that I can give you comprehensive details on how to proceed.
Regards,
Barrister Augustine Dinga
OK, for those who don’t know, it’s a variation on the classic Nigerian letter that I was getting on my fax machine 15 years ago, and by air post back around 1992. Basically, they claim to overpay and ask for a refund, sent by a method that can’t be reversed, and then the original payment, frequently a major U.S. company’s check, is found to be fake, and that’s reversed, and after that, well, federal officials show up at your door. That’s here. Over there, which might or might not be in the country claimed, it only takes one fool out of a billion spams to make you rich, and there’s no risk. Nice little business.
I usually don’t reply to these letters; they’re just too sad. But maybe, just this once:
My Dearest Augustine Dinga:
I am so saddened to hear that your friend, whom you didn’t name, by the way, has passed away. That’s probably my third cousin, twice removed, Ersatz Morgan Billy-Bob Jones Jr., who went down in a flaming trail of air cargo and land records being shipped to your country. So sad.
Yes, of course I’ll help. But I have a problem of my own. Perhaps we can help each other. There were all those flaming land records, remember? Some important ones were lost. I still have the original deed involved, of course, but I’ll need a buyer for the property, oh, and must have an overseas barrister, too, and I shoudn’t really go lower than $24 million, but I suppose for a friend of my poor crispy cousin, I could take the $23.5 million amount.
The property in question is something of a landmark, you see. Please let me know right away if you could consider buying it; it’s just massive, and a terrific income-producing structure that brings in tolls all day every day. We call it the ‘Brooklyn Bridge’.
Very Truly Yours, Etc, etc.
Jerry Stern is webmaster at PC410.com and Startupware.com.